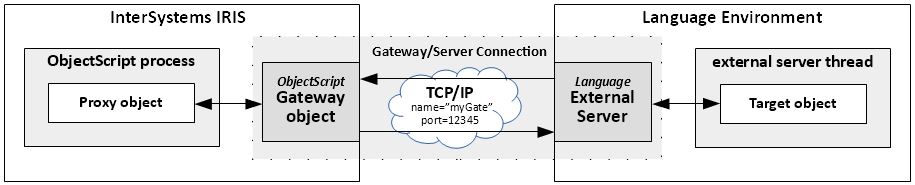
If you like Java and have a thriving Java ecosystem at work into which you need to incorporate IRIS, it's not a problem. Java External Language Gateway will do it seamlessly, almost. This gateway serves as a bridge between Java and Object Script in IRIS. You can create objects of Java classes in IRIS and call their methods. You just need a jar file to do this.
The first thing you need to do is set up the environment. To start using the Java Gateway, ensure you have the following:
- InterSystems IRIS: Installed and running.
- Java Development Kit (JDK): Installed and configured.
The second requirement may sound simple, since you're already using Java in your work, but it isn't. Thanks to this question, it turned out that you need to use JDK version 11 at the most. Which means that you need to change the version in your IDE which may case quite a bit of trouble.
Next step, we can check that everything works and try to instantiate the object of a Java system class. To do this, you have to start a connection, creat a proxy object, and call a method. Sounds like a lot of code, but in reality it's just one statement:
write $system.external.getJavaGateway().new("java.util.Date").toString()This will print the current date and time on screen.
To go further, we can create our own Java class:
public class Dish {
private String name;
private String description;
private String category;
private Float price;
private String currency;
private Integer calories;
public void setName(String name) {
this.name = name;
}
public void setDescription(String description) {
this.description = description;
}
public void setCategory(String category) {
this.category = category;
}
public void setPrice(Float price) {
this.price = price;
}
public void setCurrency(String currency) {
this.currency = currency;
}
public void setCalories(Integer calories) {
this.calories = calories;
}
public String describe() {
return "The dish "+this.name+" costs "+this.price.toString()+
this.currency+" and contains "+this.calories+" calories!";
}
}
and call it's methods from Object Script:
set javaGate = $SYSTEM.external.getJavaGateway()
do javaGate.addToPath("D:\Temp\GatewayTest.jar")
set dish = javaGate.new("Dish")
do dish.setCalories(1000)
do dish.setCategory("salad")
do dish.setCurrency("GBP")
do dish.setDescription("Very tasty greek salad")
do dish.setName("Greek salad")
do dish.setPrice(15.2)
write dish.describe()As a result we will get a string with the description of the created dish:
The dish Greek salad costs 15.2GBP and contains 1000 calories!
Quite neat, don't you think?
Anyway, learn more about using Gateways from the Documentation and good luck implementing this knowledge in your projects!

.png)
.png)